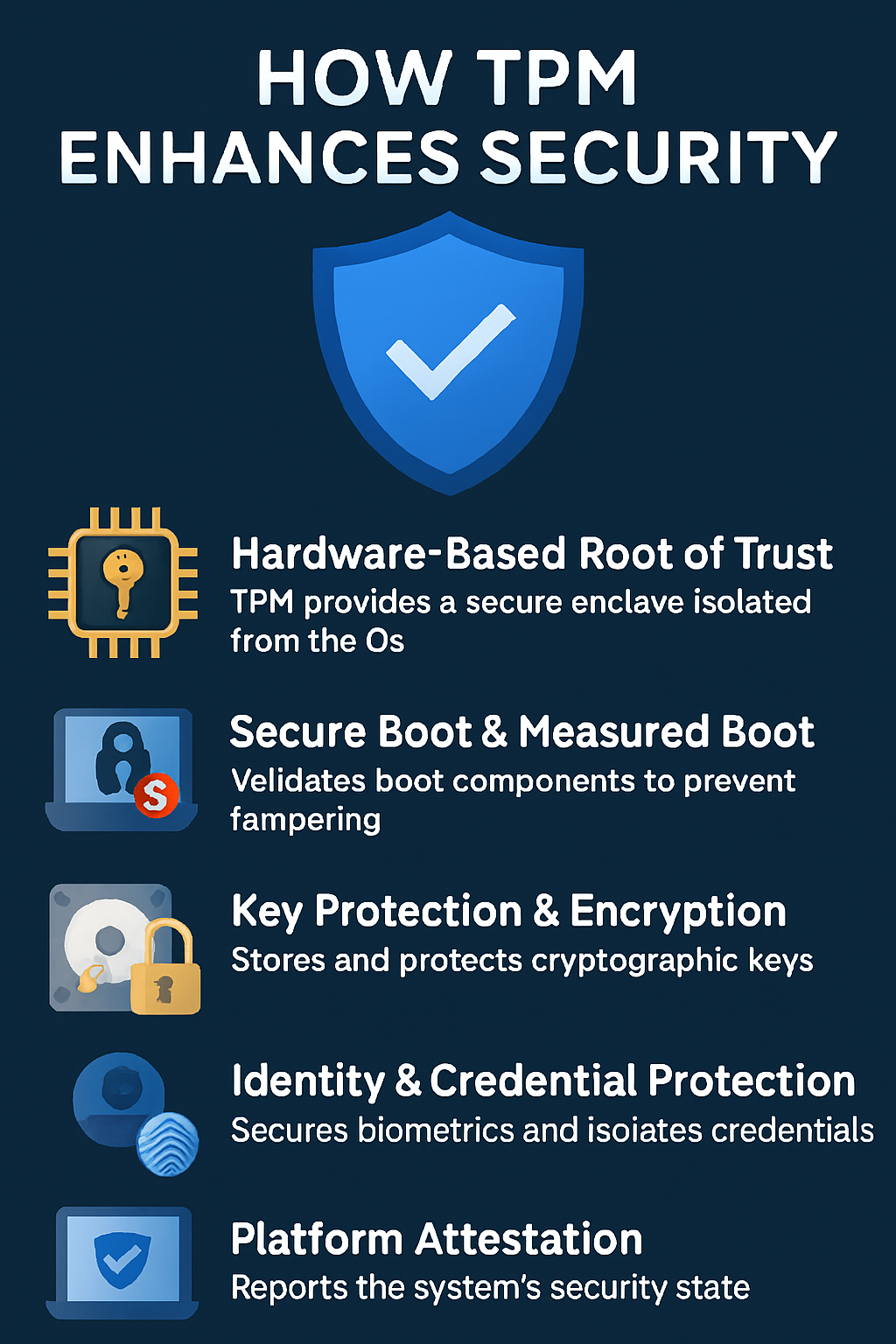
TPM is like the silent guardian of your system’s security architecture. Let’s break down how it enhances protection across different layers:
1. Hardware-Based Root of Trust
• TPM provides a secure enclave that’s isolated from the operating system.
• It stores cryptographic keys and performs operations in a tamper-resistant environment.
• Even if malware compromises the OS, the TPM remains secure and inaccessible.
2. Secure Boot & Measured Boot
• During startup, TPM verifies the integrity of boot components (like BIOS, bootloader, OS kernel).
• If any component is altered (e.g., by rootkits), TPM detects it and can halt the boot process.
• This prevents stealthy malware from loading before antivirus or OS defenses kick in.
3. Key Protection & Encryption
• TPM securely generates and stores asymmetric keys used for encryption and authentication.
• Tools like BitLocker use TPM to lock/unlock drives based on system integrity.
• Even if someone removes the hard drive, they can’t decrypt the data without the TPM.
4. Identity & Credential Protection
• TPM works with Windows Hello to store biometric data securely.
• It enables Credential Guard, which isolates login credentials from the OS.
• This blocks credential theft techniques like pass-the-hash or keylogging.
5. Platform Attestation
• TPM can report the system’s security state to remote services.
• This is used in enterprise environments for remote attestation, ensuring devices meet security standards before accessing sensitive resources.
6. Firmware and Driver Integrity
• TPM helps validate firmware updates and drivers before installation.
• This prevents malicious firmware from being injected into the system.
Why It Matters
Without TPM, your system relies solely on software-based security, which is more vulnerable to:
• Kernel-level exploits
• Bootkits and rootkits
• Credential theft
• Physical tampering
TPM adds a hardware-backed shield that’s much harder to bypass—even for sophisticated attackers.

No responses yet