Cloud is ideal when you need rapid scalability, faster time‑to‑value, and an operating‑expense model, while on‑premises fits strict data control, sovereignty, and highly predictable workloads; many organizations land on a hybrid mix to balance both benefits.[1][2][3]
Use the decision framework and comparison table below to choose cloud, on‑premise, or hybrid for your next initiative.[4][1]
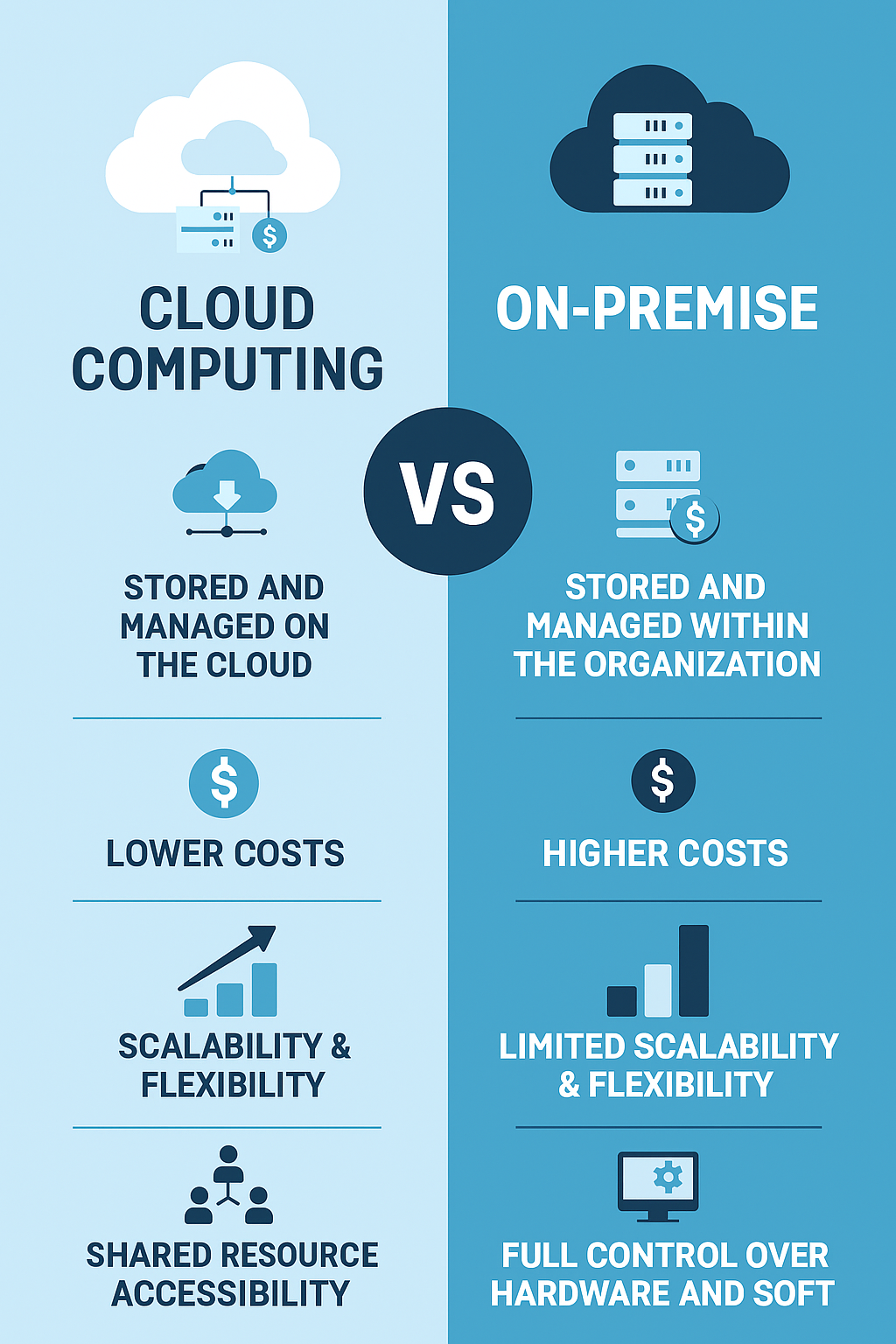
Cloud computing is a model for ubiquitous, convenient, on‑demand access to a shared pool of configurable resources that can be rapidly provisioned and released with minimal management effort or provider interaction.[5][1]
NIST highlights five essential characteristics—on‑demand self‑service, broad network access, resource pooling, rapid elasticity, and measured service—plus service models (IaaS, PaaS, SaaS) and deployment models (public, private, hybrid, community).[6][1]
On‑premises means owning and operating your own IT infrastructure and facilities, emphasizing capital expenditure for hardware/software and in‑house responsibility for lifecycle, capacity, and compliance management.[2]
The model provides maximum physical control and customization but requires staffing, upgrades, space, power, cooling, and resilience investments over time.[2]
| Dimension | Cloud computing | On‑premises |
| Ownership | Provider operates infrastructure; customers consume services via APIs and consoles [1] | Organization owns and runs hardware, software, and facilities [2] |
| Cost model | Predominantly OpEx with pay‑as‑you‑go and elasticity [2] | Predominantly CapEx with multi‑year asset lifecycle [2] |
| Scalability | Rapid, elastic scaling up/down on demand [1] | Scaling constrained by procurement cycles and installed capacity [2] |
| Security model | Shared responsibility: provider secures “of the cloud”; customer secures “in the cloud” [4] | Organization responsible for end‑to‑end security controls [2] |
| Reliability/SLA | Formal service SLAs (e.g., EC2 region‑level availability targets) [7] | Availability depends on local architecture, redundancy, and operations [2] |
| Compliance/data location | Regional choices and residency features support regulatory needs [3] | Full locality control; responsibility to implement compliance controls [3] |
| Time‑to‑value | Fast provisioning and managed services accelerate delivery [1] | Longer lead times for procurement, installation, and integration [2] |
| Lock‑in/portability | Service choices can affect portability and switching costs [8] | Hardware/software commitments can also create inertia [2] |
| Deployment models | Public, private, hybrid, community per NIST taxonomy [1] | Typically private, with optional extensions to cloud (hybrid) [1] |
Cloud shifts spend from CapEx to OpEx, which can improve cash flow and align costs with usage, especially for variable or bursty workloads.[2]
On‑premises TCO must include hardware refreshes, facilities, staffing, support contracts, and contingency planning, which can exceed initial purchase assumptions if not fully modeled.[2]
Cloud security follows a shared responsibility model: the provider secures infrastructure, while customers configure and secure workloads, identities, data, and network policies.[4]
Regulated workloads often require data residency and sovereignty controls; providers offer regional choices and documentation, and organizations remain accountable for lawful processing and protective measures.[3][9]
Major cloud providers publish service SLAs and offer service credits if availability commitments are not met, with EC2 defining both instance‑level and region‑level uptime constructs.[7]
Architecting across Availability Zones and regions is recommended to meet higher availability targets than any single instance or site can provide.[7]
Cloud regions and zones enable placing workloads closer to users and data while leveraging managed services for consistent performance at scale.[7]
On‑premises can deliver ultra‑low latency for local systems and specialized hardware, but global reach typically requires additional investment or hybrid designs.[2]
- Demand fluctuates or grows unpredictably, making elasticity and pay‑as‑you‑go compelling.[1][2]
- You want to accelerate delivery using managed databases, analytics, and platform services to reduce undifferentiated heavy lifting.[1]
- You need published SLAs and the ability to design for multi‑AZ/region resiliency without building new data centers.[7]
- Strict data sovereignty, locality, or specialized compliance requires full environmental control.[9][3]
- Ultra‑low latency to factory floors, trading venues, or embedded systems is paramount and not easily met by remote regions.[2]
- Workloads are stable and predictable, and existing facilities and teams are optimized for current scale.[2]
NIST recognizes hybrid deployment, combining on‑premises and cloud to place each workload where it fits best.[1]
Hybrid addresses sovereignty and latency while using cloud for elasticity, and multi‑cloud can mitigate concentration risk and align services to strengths by provider.[3][1]
Migration strategies (the “Rs”)
AWS prescriptive guidance expands classic migration options into seven strategies: Retire, Retain, Rehost, Relocate, Repurchase, Replatform, and Refactor/Re‑architect, each balancing speed, cost, and modernization.[8]
Choosing among the Rs depends on business drivers, technical fit, and target operating model, and can evolve per application portfolio segment.[8]
- Regulatory: Do residency/sovereignty laws constrain where data and processing must live ?[9][3]
- Demand profile: Is workload spiky or seasonal versus steady and predictable ?[1][2]
- Time‑to‑value: Do managed services significantly compress delivery timelines ?[1]
- Reliability: Are published SLAs and cross‑AZ/region designs needed or can local HA suffice ?[7]
- Cost model: Is OpEx alignment with usage preferable to CapEx investment at current stage ?[2]
- Operating model: Do you want shared responsibility with provider or full in‑house control ?[4]
- Portability: Will service choices hinder future portability or refactoring effort ?[8]
Adopt cloud services that match workload patterns, starting with rehost/replatform to gain quick wins, then refactor where modernization pays back in resilience and efficiency.[8]
For sensitive datasets, enforce regional controls and data minimization, and document controls against applicable frameworks and obligations.[3][4]
Q: Is cloud always cheaper than on‑premises
A: Not always; cost depends on utilization, architecture, and governance, with cloud favoring elastic demand and on‑prem often fitting stable, high‑utilization workloads when fully loaded costs are considered.[2]
Q: How do SLAs translate to my uptime
A: Provider SLAs set service targets and credits, but your architecture—multi‑AZ, multi‑region, and failover design—ultimately determines experienced availability.[7]
Q: Can hybrid satisfy sovereignty and modernization
A: Yes, hybrid lets regulated data stay on‑premises while using cloud for scalable compute and managed services, provided controls and residency requirements are met.[9][3][1]
- https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-145.pdf
- https://www.cloudzero.com/blog/capex-vs-opex/
- https://www.ibm.com/think/insights/data-residency-why-is-it-important
- https://aws.amazon.com/compliance/shared-responsibility-model/
- https://csrc.nist.gov/pubs/sp/800/145/final
- https://www.nist.gov/publications/nist-definition-cloud-computing
- https://aws.amazon.com/compute/sla/
- https://docs.aws.amazon.com/prescriptive-guidance/latest/large-migration-guide/migration-strategies.html
- https://www.oracle.com/middleeast/security/saas-security/data-sovereignty/data-sovereignty-data-residency/
- https://www.nist.gov/document/nist-sp-500-322-evaluation-cloud-computing-services-based-nist-800-145
- https://csrc.nist.rip/publications/nistpubs/800-145/SP800-145.pdf
- https://secureframe.com/frameworks-glossary/nist-800-145
- https://www.commvault.com/blogs/aws-shared-responsibility-model-what-you-need-to-know
- https://www.archive360.com/blog/revisited-capex-versus-opex-on-premises-versus-the-cloud
- https://thorteaches.com/glossary/nist-sp-800-145/
- https://docs.aws.amazon.com/whitepapers/latest/introduction-devops-aws/shared-responsibility.html
- https://dl.acm.org/doi/book/10.5555/2206223
- https://amzur.com/blog/comparing-capex-opex-cloud-models/
- https://www.thecre.com/fisma/?p=737
- https://docs.aws.amazon.com/wellarchitected/latest/security-pillar/shared-responsibility.html
- https://thisismydemo.cloud/post/capex-subscription-tco-modeling-hyper-azure-local-avs/
- https://sprinto.com/glossary/nist/nist-800-145/
- https://docs.aws.amazon.com/whitepapers/latest/aws-risk-and-compliance/shared-responsibility-model.html
- https://www.cloudoptimo.com/blog/understanding-total-cost-of-ownership-tco-in-cloud-computing/
- https://www.kiteworks.com/gdpr-compliance/understand-and-adhere-to-gdpr-data-residency-requirements/
- https://www.exoscale.com/blog/cloudact-vs-gdpr/
- https://spacetime.eu/blog/who-really-owns-your-data-comparing-european-sovereign-cloud-providers/
- https://milvus.io/ai-quick-reference/how-do-cloud-providers-support-compliance-with-gdpr-and-ccpa
- https://www.logicata.com/blog/aws-service-level-agreement/
- https://www.stormit.cloud/blog/6-rs-aws-migration-strategies/
- https://aws.amazon.com/blogs/enterprise-strategy/6-strategies-for-migrating-applications-to-the-cloud/
- https://cpl.thalesgroup.com/faq/data-security-in-the-cloud/how-do-i-enforce-data-residency-policies-in-the-cloud-and-specifically-comply-with-gdpr
- https://aws.amazon.com/ec2/sla/historical/
- https://stonefly.com/blog/data-sovereignty-vs-data-residency-compliance-guide/
- https://aws.amazon.com/legal/service-level-agreements/
- https://docs.aws.amazon.com/prescriptive-guidance/latest/application-portfolio-assessment-guide/iterating-6-rs-migration-strategy-selection.html
- https://techgdpr.com/blog/server-location-gdpr/
- https://www.amazonaws.cn/en/ec2/sla/ningxia/
- https://www.leanix.net/en/wiki/tech-transformation/6rs-of-cloud-migration
- https://www.impossiblecloud.com/magazine/gdpr-compliant-cloud-storage

No responses yet